Core Concepts
Control Plane
Configure inbound management services (WinBox, SSH, API) and firewall rules at scale in Altostrat.
Default Policy
When you sign up, Altostrat automatically creates a Default Control Plane Policy for basic protection. This policy includes:- Trusted Networks (e.g., private IP ranges like 10.x, 192.168.x)
- WinBox, API, and SSH enabled on default ports
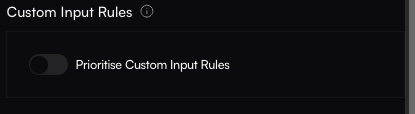
- Custom Input Rules toggled on or off
The IP address
154.66.115.255/32 may be added by default as a trusted address for Altostrat’s Management API.Creating a Control Plane Policy
1
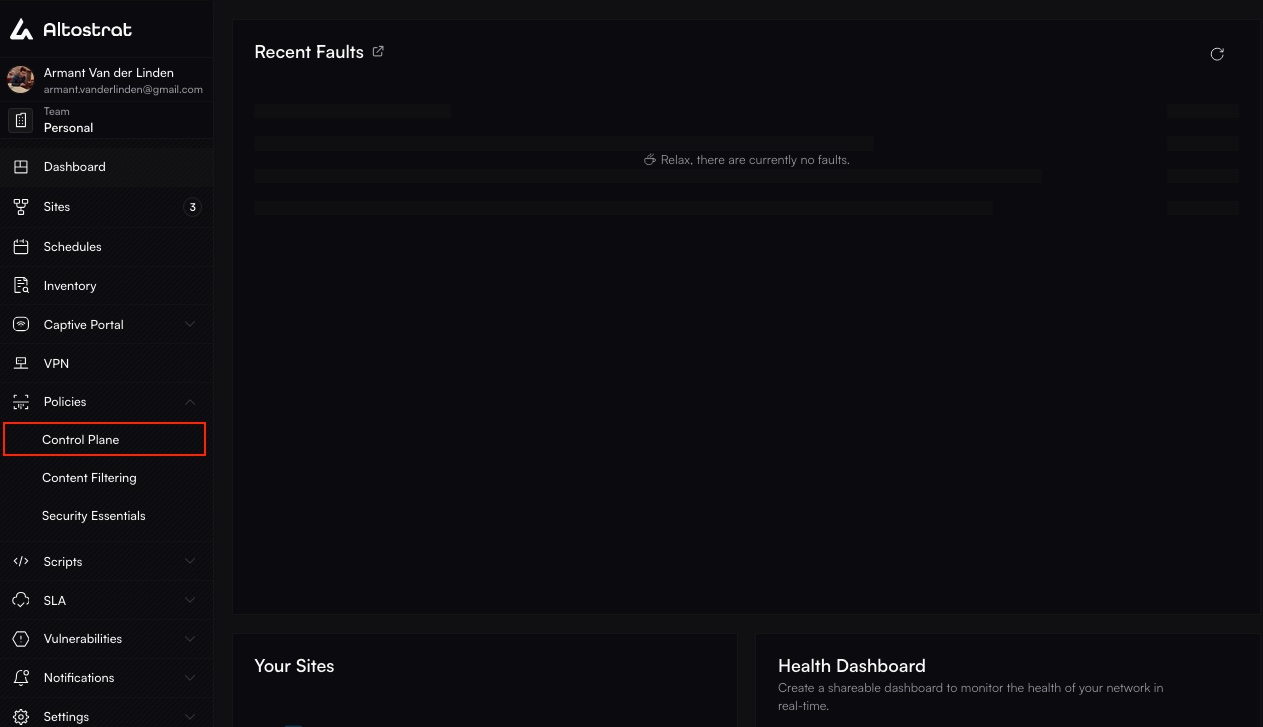
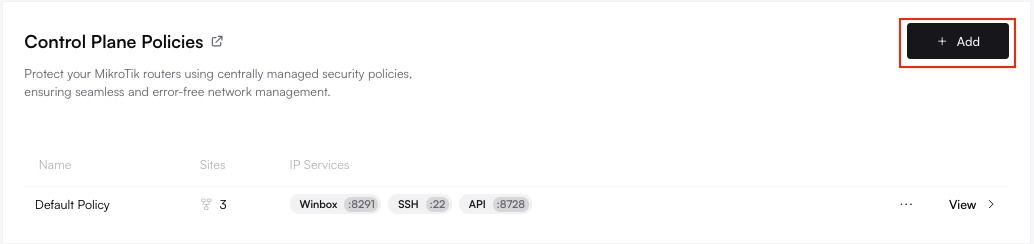
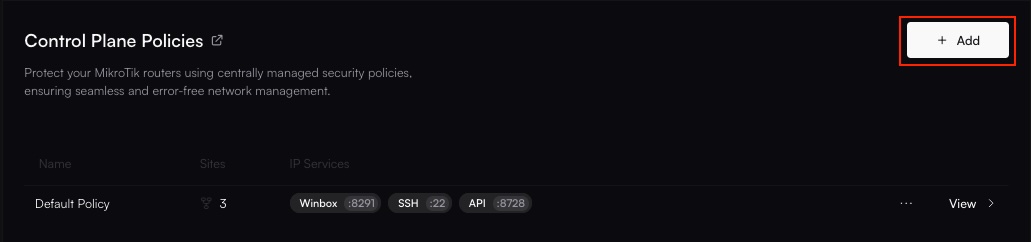
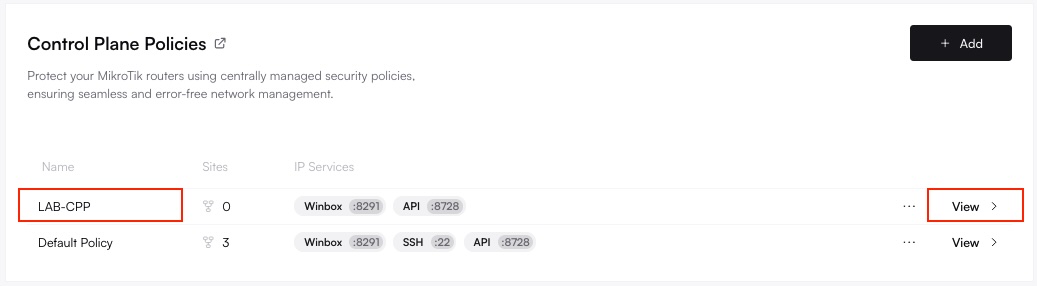
Navigate to Control Plane Policies
Under Policies, select Control Plane. You’ll see a list of existing policies, including the default one.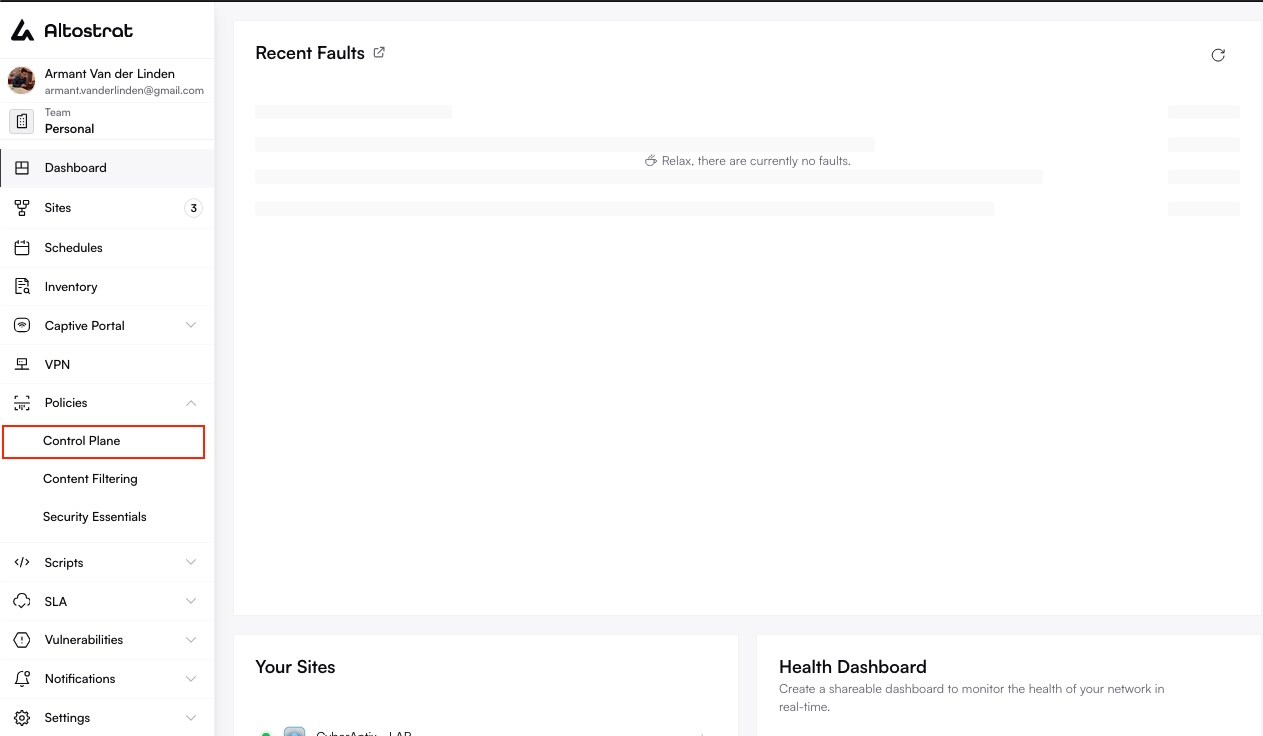




2
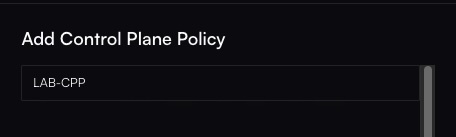
Add a New Policy
Click + Add Policy. Give your policy a descriptive name (e.g., “Strict Admin Access”).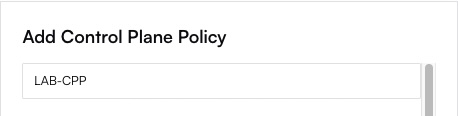


3
Configure Trusted Networks
Add or remove IP addresses or CIDR ranges that you consider trusted. For example: 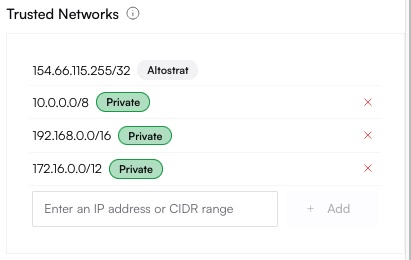
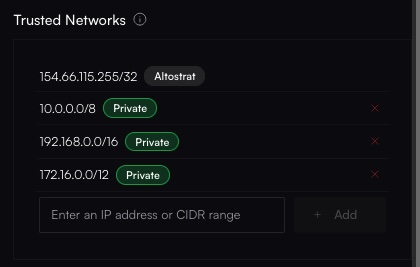
192.168.0.0/16.

4
Toggle Custom Input Rules
Decide whether your MikroTik firewall input rules should take precedence. If set to ON, your custom rules will be applied first.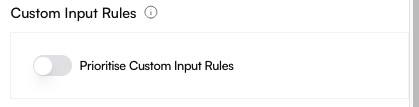


5
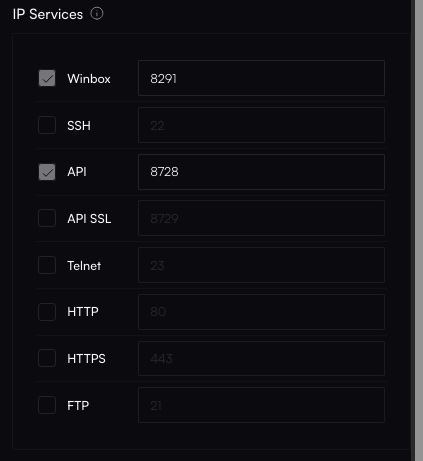
Enable/Disable Services
Under IP Services, specify ports for WinBox, SSH, and API. These services must remain enabled if you plan to manage devices via Altostrat’s API.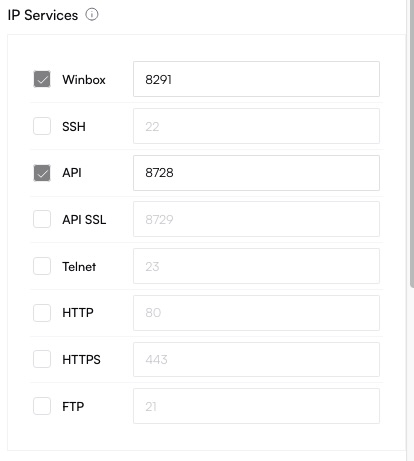


6
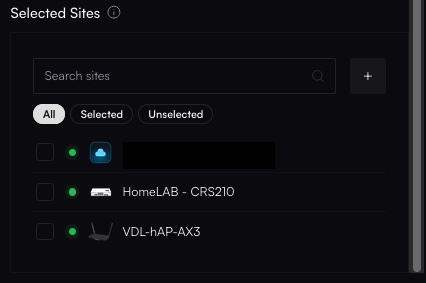
Select Sites
Assign the policy to specific sites if desired. You can also assign it later. Click Add to finalize.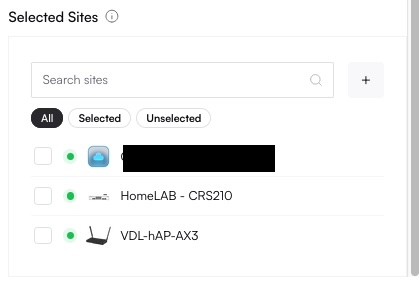


Editing a Control Plane Policy
1
Locate the Policy
Navigate to Policies → Control Plane. Click on the policy to open its settings.





2
Adjust Trusted Networks or Services
Add or remove CIDRs, toggle whether Custom Input Rules override Altostrat’s default drop rules, and modify ports for WinBox, API, and SSH.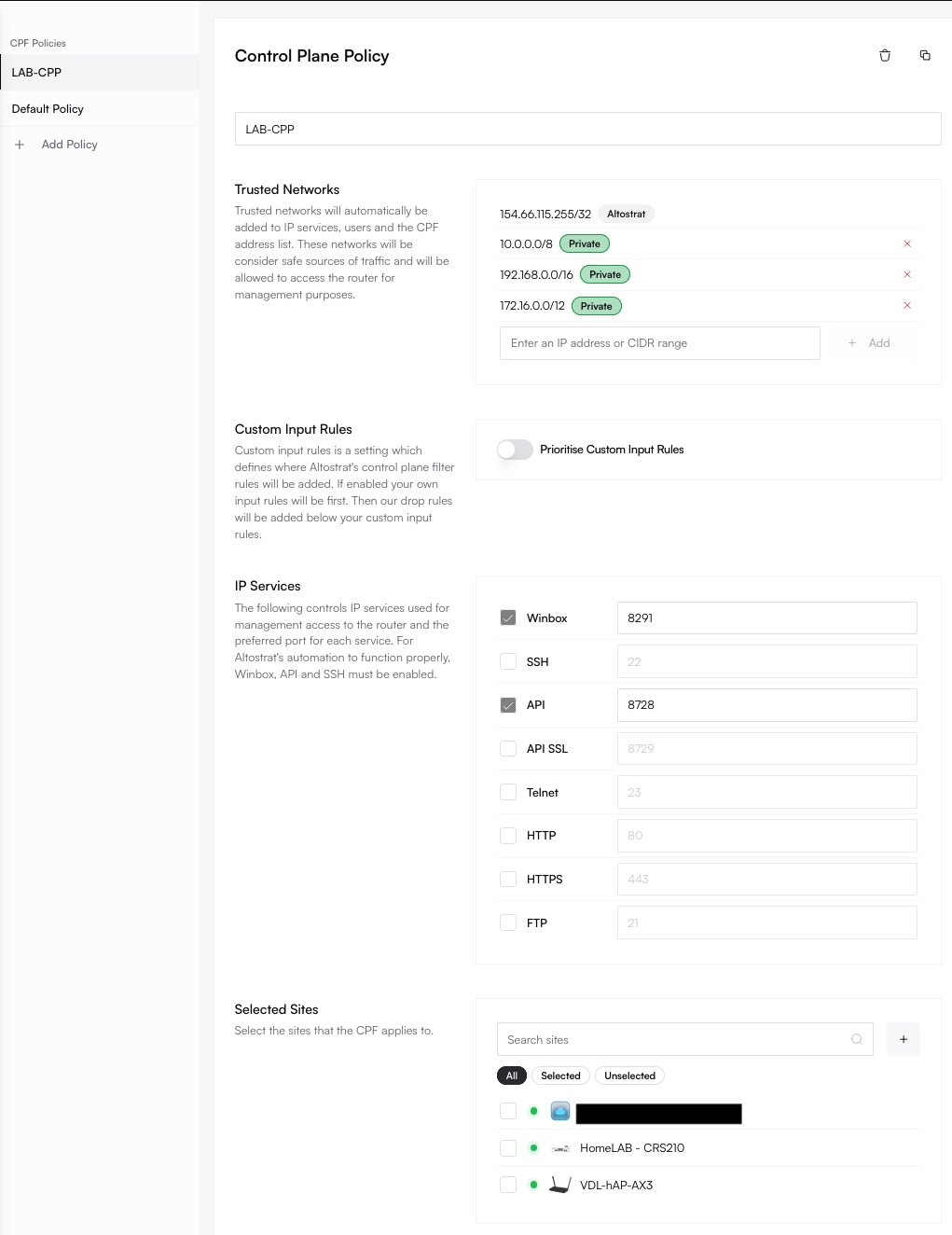


3
Apply Changes
Changes will propagate automatically to any sites using this policy. Allow a short period for routers to update.
Removing a Control Plane Policy
Deleting a policy from an active site may disrupt management access if no other policy is assigned.
1
Find the Policy
In Policies → Control Plane, locate the policy you wish to remove.



2
Delete the Policy
Click the Trash icon and confirm the action. If any routers depend on this policy for inbound admin services, assign them another policy first.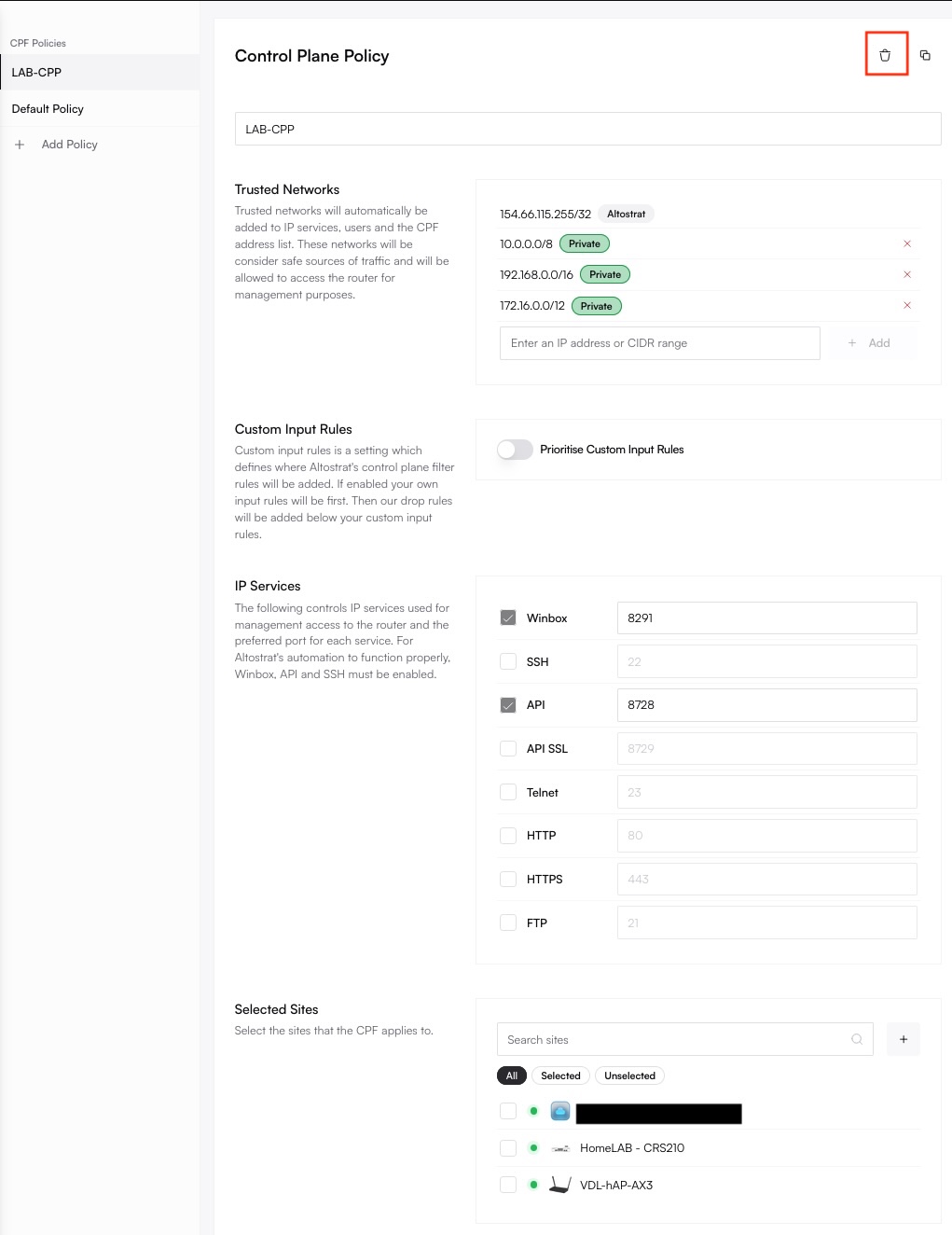


Best Practices
- Maintain Essential Services: Keep WinBox, SSH, and API enabled if you plan to manage devices through Altostrat.
- Limit Trusted Networks: Restrict access to reduce exposure.
- Regular Review: Review and update policies as your network changes.
- Security Layering: Combine with Security Essentials for a comprehensive security approach.

