Core Concepts
Threat Feeds
Leverage BGP-delivered threat intelligence feeds to automatically block malicious traffic at your network edge.
Altostrat’s Threat Feeds feature enhances network security by integrating curated threat intelligence lists directly into your MikroTik router’s routing table or firewall, often using BGP mechanisms. This allows you to automatically block traffic to and from known malicious IP addresses associated with threats like botnets, scanners, and compromised servers by null-routing or filtering traffic based on these feeds.
This feature complements DNS-based Content Filtering, providing protection at the IP/routing layer. Both features are often managed under the same policy framework within Altostrat.
To stop applying a policy to a specific site without deleting the policy definition, navigate to the site’s configuration and assign a different Threat Feed policy or remove the current assignment (Remove BGP policy from site via API).
Key Features
- BGP-Delivered Threat Intelligence: Utilize automatically updated lists of malicious IP addresses sourced from reputable providers (e.g., Team Cymru, FireHOL, Emerging Threats), often distributed via BGP.
- Automated Routing/Firewall Integration: Selected threat feeds dynamically update the router’s configuration, typically by adding routes pointing to a null interface (blackhole) or populating firewall address lists for blocking rules.
- Malicious Traffic Blocking: Prevent inbound and outbound connections associated with known threats based on the subscribed feeds at the network layer.
- Logging and Monitoring: Track policy update statuses via the Orchestration Log and monitor related routing or firewall events on the MikroTik device.
Default Threat Feed Policy
When you first sign up, Altostrat may create a default Threat Feed Policy incorporating essential Threat Feeds. This policy often includes lists such as:- RFC 1918 Private IP Ranges (common bogon filtering)
- Team Cymru FullBogons (unallocated/unroutable IP addresses)
- FireHOL Level 1 (basic list of known malicious IPs)
- Emerging Threats Block IPs (compromised IPs, C&C servers)
Creating a Threat Feed Policy
1
Navigate to Threat Feeds Policies
Go to Policies → Threat Feeds in the Altostrat portal.


2
Add a New Threat Feed Policy
Click Add or + New. Enter a descriptive policy name (e.g., “Block Known Attackers”, “Critical Infrastructure Feeds”).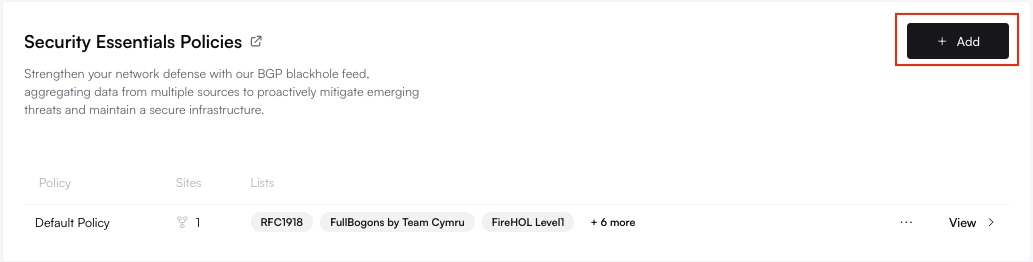


3
Select Threat Feeds (BGP/DNR Lists)
Choose the specific threat intelligence feeds (BGP/DNR Lists) you want to enable within this policy. The available feeds can be viewed (View available BGP/DNR lists via API). Select feeds based on desired protection level and potential operational impact.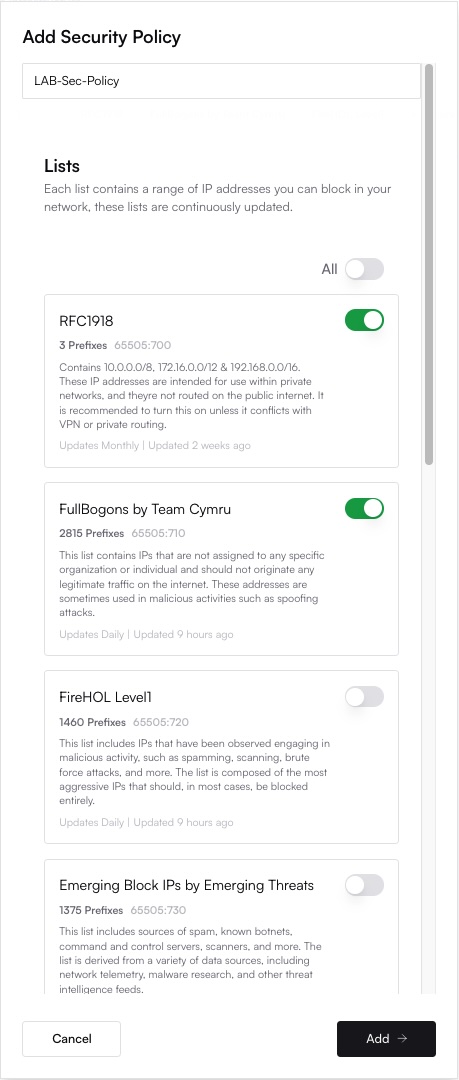


4
Save and Apply Policy
Click Save or Add to finalize the policy definition (Create BGP policy via API). To apply it to a site:
- Navigate to the desired Site overview page.
- Assign this newly created policy under the site’s Threat Feed Policy setting. (Assign BGP policy to site via API).
- The router will then be configured (via the Management VPN) to utilize the selected BGP feeds, updating its routing table or firewall rules. Allow time for synchronization.
Editing a Threat Feed Policy
1
Navigate to Threat Feeds Policies
Access the Altostrat portal and navigate to Policies → Threat Feeds.



2
Select the Threat Feed Policy to Edit
Click on the name of the policy you wish to modify. Toggle the desired threat feeds (BGP/DNR Lists) on or off as needed within the policy configuration.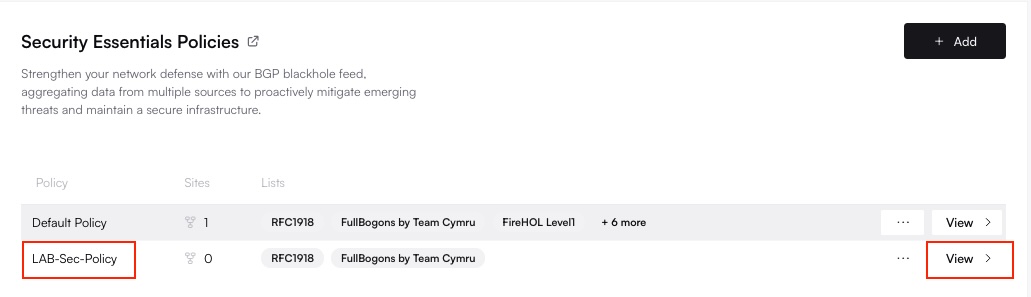
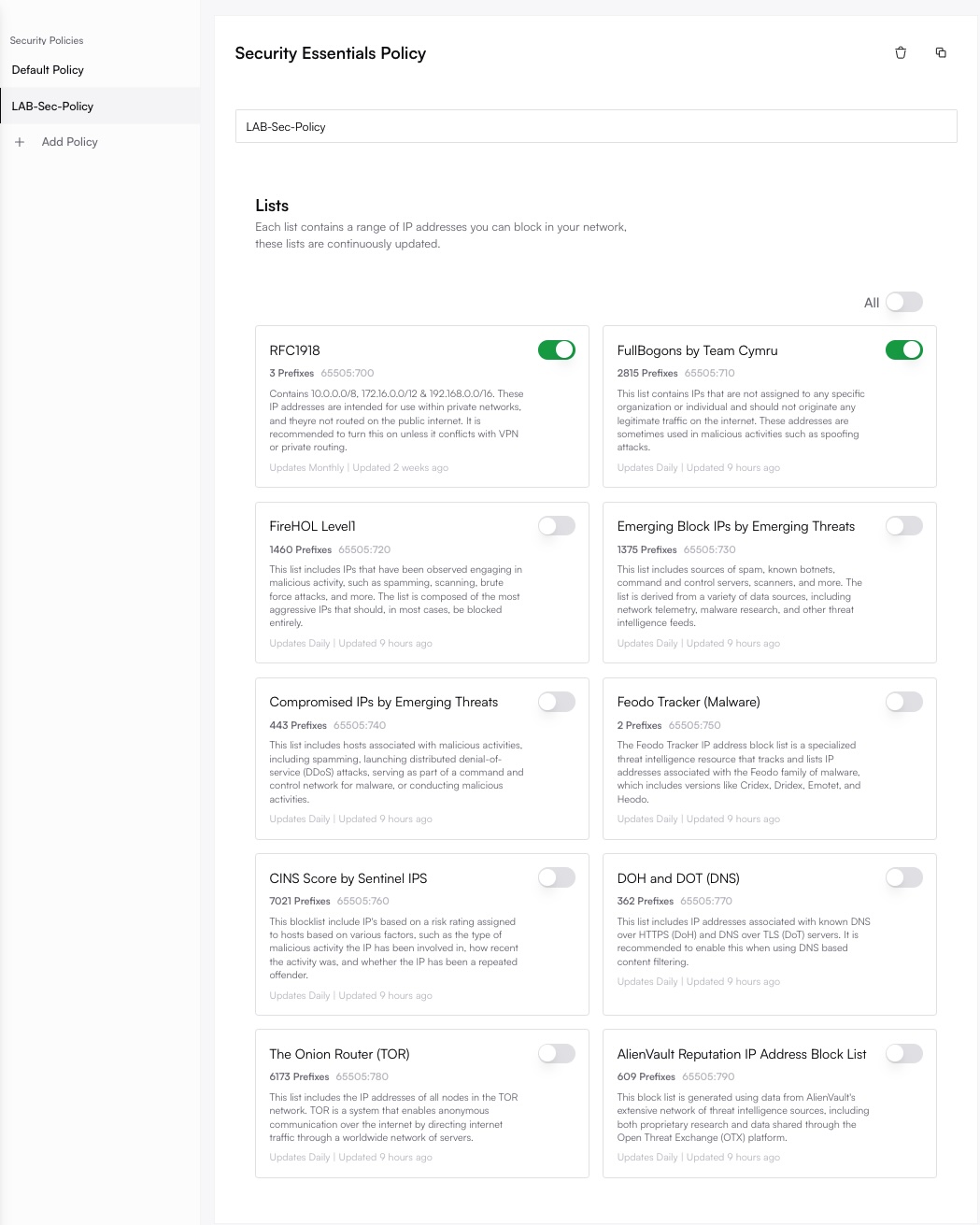




3
Save Changes to Propagate
Click Save or Update. Changes automatically propagate to all sites using this policy, updating their routing/firewall configurations. (Update BGP policy via API).
Removing a Threat Feed Policy
Deleting a Threat Feed Policy also removes its configuration from any sites using it. This disables the associated routing or firewall rules derived from its feeds, potentially increasing the site’s exposure to threats if no alternative protection is active.
1
Navigate to Threat Feeds Policies
Go to Policies → Threat Feeds and identify the policy you want to delete.



2
Delete the Threat Feed Policy
Click the Remove or Trash icon next to the policy and confirm your choice. This deletes the policy definition itself. Sites previously using it will have the corresponding configurations removed. (Delete BGP policy via API).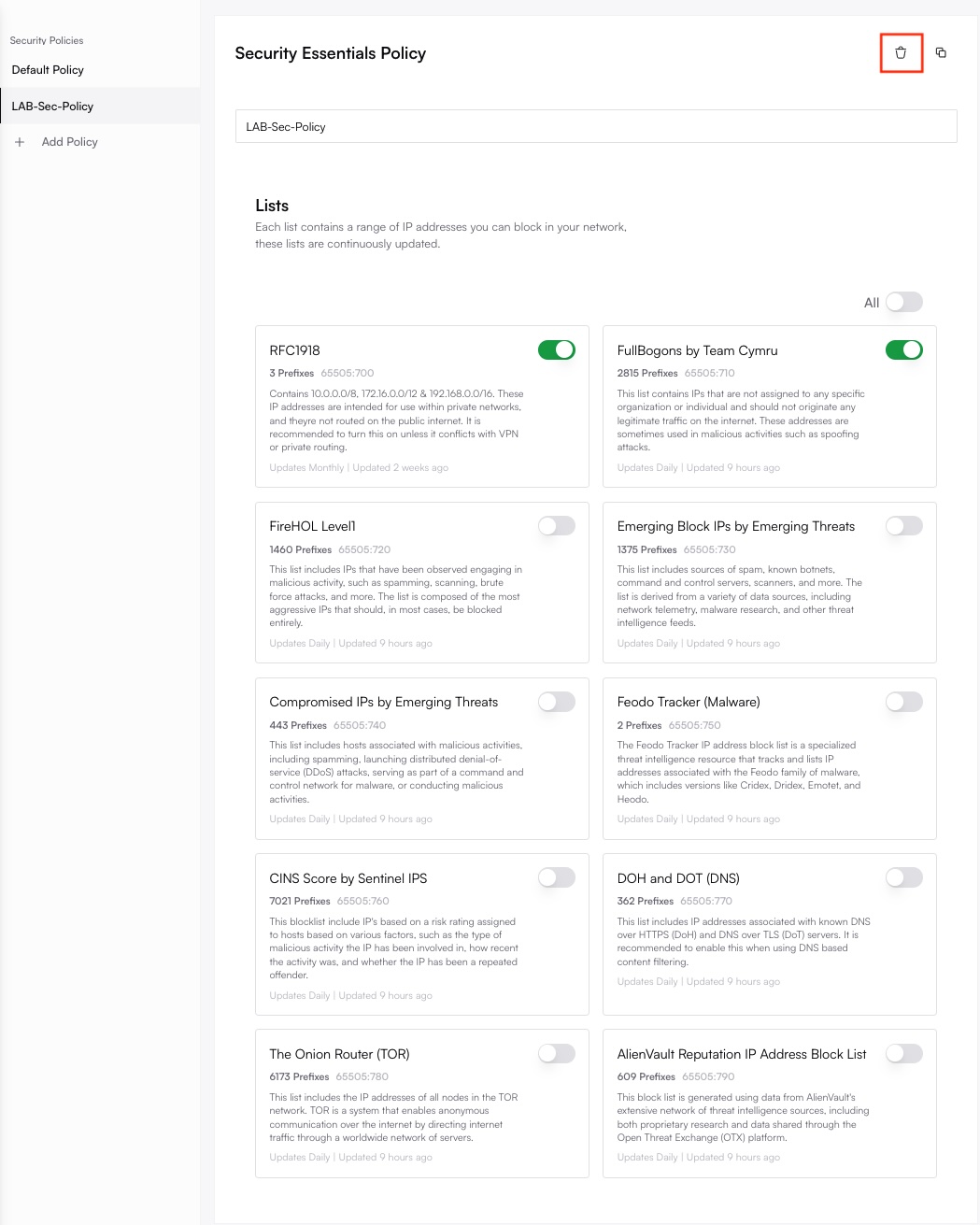


Programmatic Management (Threat Feed Policy API)
Threat Feed policies using BGP/DNR can be managed programmatically via the Altostrat API. Key endpoints include:- Create BGP Policy:
POST /bgp/policy(API Docs) - List BGP Policies:
GET /bgp/policy(API Docs) - Get BGP Policy Details:
GET /bgp/policy/{policy}(API Docs) - Update BGP Policy:
PUT /bgp/policy/{policy}(API Docs) - Delete BGP Policy:
DELETE /bgp/policy/{policy}(API Docs) - Assign BGP Policy to Site:
POST /bgp/{site_id}(API Docs) - Remove BGP Policy from Site:
DELETE /bgp/{site_id}(API Docs) - List Available BGP/DNR Feeds:
GET /bgp/category(API Docs)
Best Practices
- Understand Feed Sources: Know the origin and nature of each BGP/DNR feed (e.g., bogons, active threats) to assess potential impact and false positive risks.
- Monitor Routing/Firewall Impact: Check the router’s routing table (for blackholes) and firewall logs/rules to see how the feeds are being implemented and what traffic is being blocked.
- Start Selectively: Implement conservative feeds first (like bogon lists) before adding more aggressive threat feeds. Monitor network reachability closely after adding new feeds.
- Layered Security: Use Threat Feeds (IP/BGP layer) in conjunction with Content Filtering (DNS layer) for comprehensive protection.
- Regular Audits: Periodically review feed selections and policy assignments to align with current security needs and threat landscape.

