Integrations
Microsoft Azure Integration
Use Microsoft Entra (Azure AD) for secure user authentication in Altostrat.
Leverage Microsoft Entra (formerly Azure AD) for user logins in Altostrat. This guide explains how to register an app in the Azure portal, get the client credentials, and integrate them into Altostrat for OAuth 2.0 flows.
Prerequisites
- Microsoft Azure subscription with access to Entra ID (Azure AD).
- Sufficient privileges in Altostrat to configure identity providers.
Part 1: Azure Portal Setup
1
Log into Azure Portal
Go to https://portal.azure.com and sign in.
Use global search to find Microsoft Entra ID or Azure Active Directory.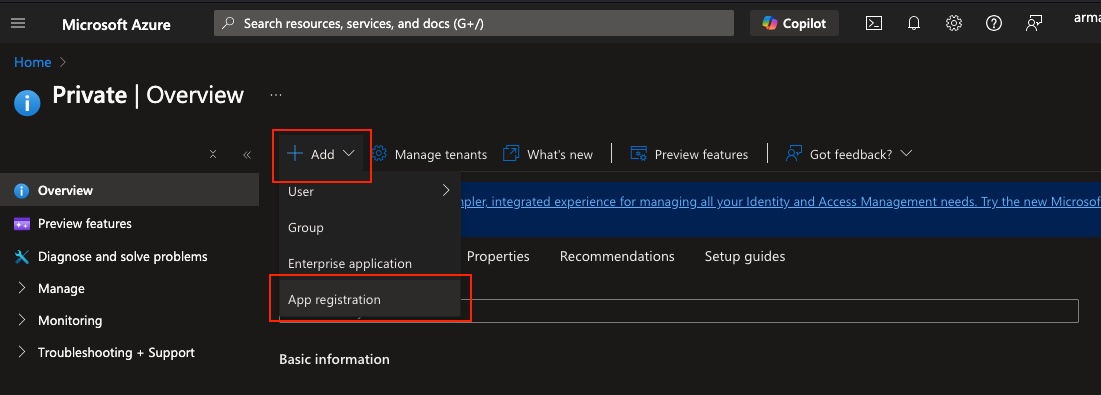

2
Create App Registration
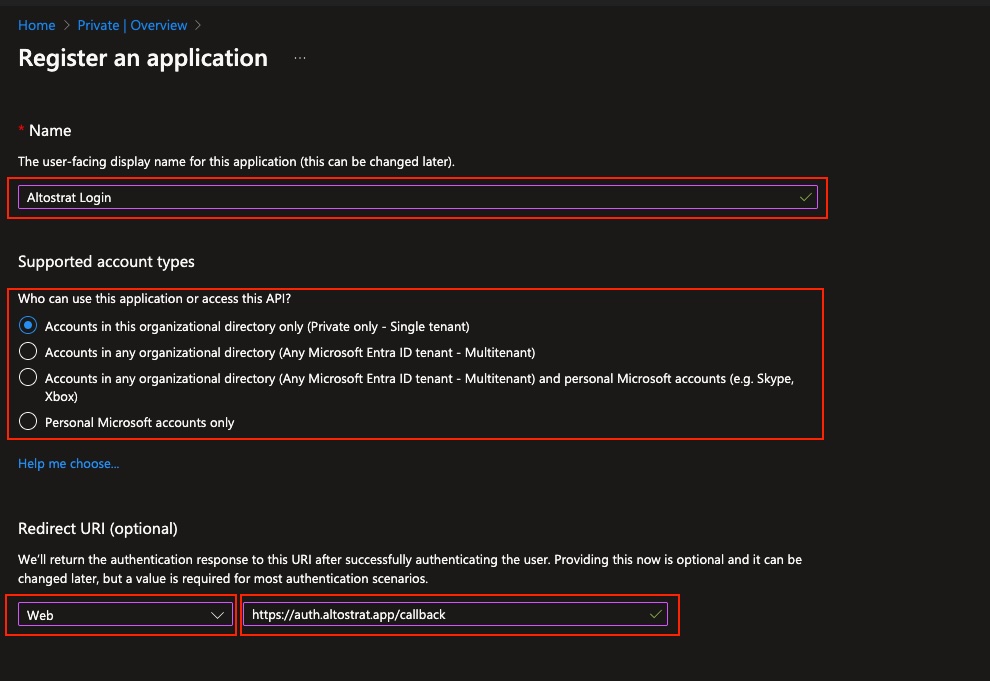
- In the Entra ID (Azure D) overview, click App registrations.
- Select + New registration to create a new application.
- Name the app (e.g., “Altostrat Login”) and choose Supported account types.
- Under Redirect URI, pick Web and
enter
https://auth.altostrat.app/callback.

3
Register and Note Credentials
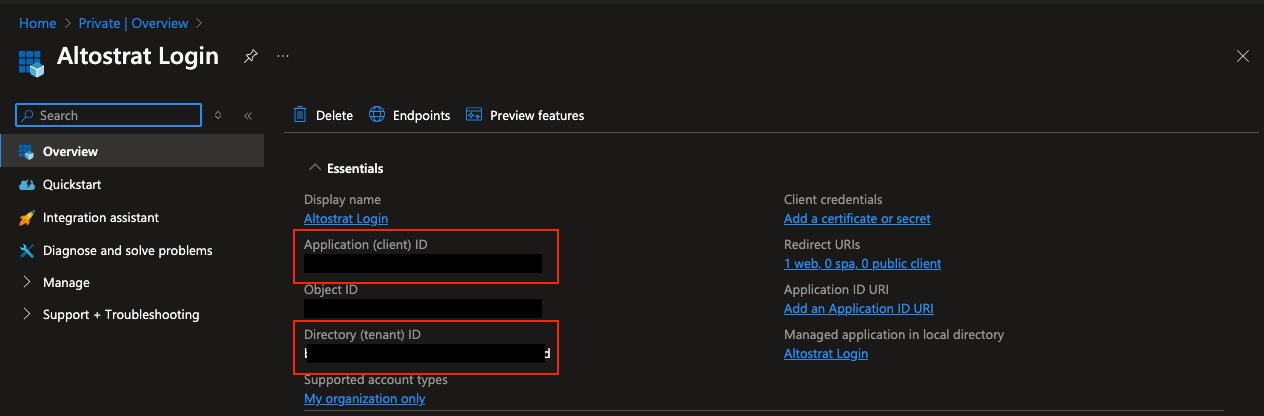
- After registering, note the Application (client) ID and Directory (tenant) ID.

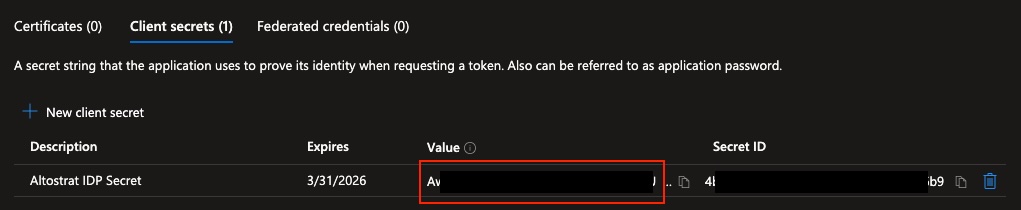
- Go to Certificates & secrets to generate a Client Secret. Copy the secret’s value immediately.

You won’t be able to view the client secret again after leaving the page. Store it in a safe place.
Part 2: Altostrat Configuration
1
Open Integrations in Altostrat
From the Altostrat dashboard, choose Captive portal → Identity Providers.


2
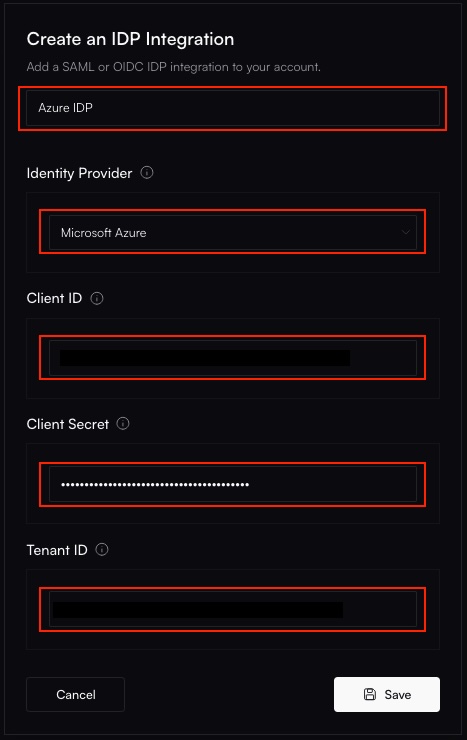
Add Azure Credentials
Fill in the Client ID (Application ID), Client Secret, and Tenant ID from your Azure
app registration.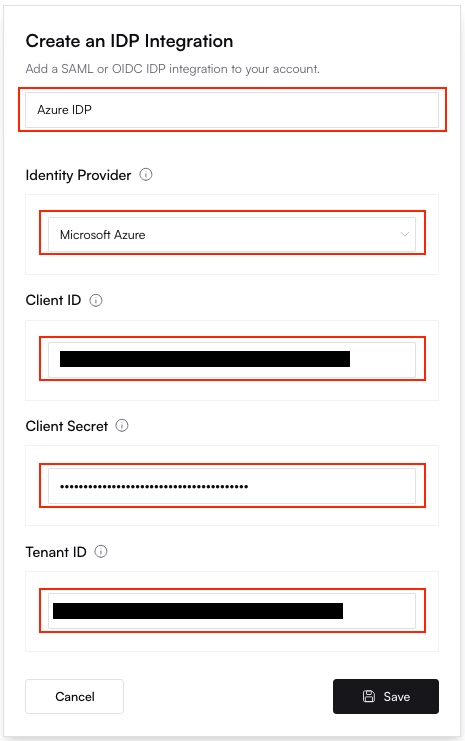


3
Save & Test
Click Save, then perform a test sign-in to ensure Altostrat redirects to Azure and back
successfully.
Troubleshooting
- Redirect URI Mismatch
Ensure
https://auth.altostrat.app/callbackmatches the one in your Azure app. - Invalid Client Secret If you see authentication errors, regenerate a new secret in Certificates & secrets, then update Altostrat.
- User Domain Restrictions If you set Single Tenant in Azure, only users from your tenant can log in. For external users, you need Multi-Tenant or Personal Accounts enabled.
- Check Orchestration Logs Failed logins or token errors appear in the Orchestration Log.
Updating or Removing the Integration
- Azure Portal Modify or delete the app registration if you need to rotate secrets or allow different account types.
- Altostrat In Integrations, remove or edit the Microsoft Azure entry. If removed, users depending on Azure AD can’t log in until another method is configured.
Deleting the integration breaks any user logins that rely on Microsoft Entra credentials. Have a fallback admin
account if needed.

